Rethinking SCADA Security in the Age of Terrorism
By Doug Fitzgerald
Most supervisory control and data acquisition (SCADA) systems, depending on their sophistication and type, were designed to allow a single individual to monitor critical functions of a municipal water plant and to control many of those processes from one or more locations. Their basic purpose was to improve efficiency, giving better system control with less manpower - a job that they continue to do as well as ever.
While the need for such systems has remained the same, the world was changed inalterably by the events of Sept. 11 and its aftermath. Now, the water industry must look at the control offered by SCADA systems not only as source of improved efficiency, but also as a potential avenue for terrorists who may seek to infiltrate the systems for destructive purposes.
The industry must now take steps to ensure that the concentrated process-control power afforded by the SCADA system remains in the proper hands.
Hazards of Remote Interconnection
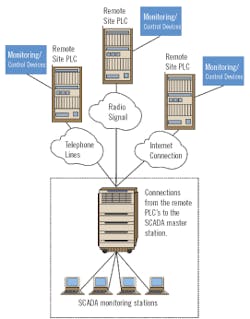
SCADA systems and related programmable logic controllers (PLCs) have been used for many years in various types of site-specific applications without compromising system security. The potential for mischief was increased dramatically when industry began to interconnect these systems to remote locations. Once that occurred, the door was opened for others to gain access to the system without the knowledge of central control-station personnel. Access to the SCADA might be gained from a remote, unmanned location such as pumping station, a water tower or a finished water-storage area - anywhere that the system can be accessed out of sight of authorized employees.
In some cases, those who installed the SCADA systems may have built in a "back door" link for the purpose of maintenance and troubleshooting, which provides still another way to enter the system from afar for possible criminal purposes.
Shutting the Door on Outsiders
A SCADA system can be connected to remote locations in various ways, including radio signals, dedicated phone lines and the Internet. Whatever the method of communication used, the first order of business in terms of improving security is to somehow break this link to the outside world for those who should not have access.
Radio signals are particularly susceptible to curious people who use simple scanners to detect the frequency in use and then tune in at will. Therefore, companies employing radio signals for their systems will need to look at ways to scramble or encrypt those signals to make it more difficult to intercept information.
Diagnostic "back doors" that are designed to let system manufacturers dial into the system for troubleshooting can be closed to interlopers by installing protective "callback" measures. With such a provision, no matter who succeeds in calling into the system, the system will only call back to certain pre-programmed locations, thus thwarting a would-be troublemaker.
Connections to manufacturers also can be limited to hard-wire hook-ups, which employ a key switch that must be physically actuated by a water-plant employee before the manufacturer gains access to the system.
Compartmentalizing a system, so that access can be granted to one segment but denied to remaining segments, also can make it more secure. This usually can be accomplished by use of multiple codes for access to different areas.
Finding System Weaknesses
Since no two SCADA systems are alike, the only way to accurately diagnose security needs is to put experts to work in an attempt to "crack" a given system. Usually, best results are obtained when outside consultants are teamed with in-plant experts in an effort to probe the entire network for weak spots. This process involves examining the full scope of system architecture - exploring all system components and infrastructure, and sometimes tracing every individual wire.
Once that is complete, consultants and system operators can begin looking for methods to physically safeguard the system, including various locking hardware devices and tamper-proofing measures. Then they are ready to analyze the need to restrict access via whatever electronic portals may exist.
An exhaustive security survey not only will lead to the installation of new security measures and systems, but also usually will reveal a need for a general tightening of security awareness and procedures. It is only human nature that over time employees and management will become less vigilant regarding routine practices and methods. Personnel must be reminded of the importance of observing everyday security precautions, such as using log-on codes and remembering to log off when a task is completed.
In the post-Sept. 11 world, we must not only use SCADA systems to keep facilities operating smoothly and efficiently, but also must take measures to see that the SCADA system is not used against us. Ask yourself: are you maintaining control of your own controls?