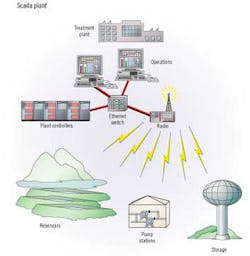
Water Security: The Role of the SCADA System
By Kevin Finnan
With assessments and implementation of appropriate security measures receiving the full attention of the water industry, many utilities have a vision of an ideal monitoring system that is networked throughout their entire operation.
The system would provide constant monitoring of all vulnerable areas. It would immediately report any security breaches or abnormal operating conditions. It would limit the need for regular patrols and drastically reduce the frequency of visits to remote sites. The system would be tolerant of efforts to defeat it. The system also would be able to automatically react to conditions and perform control actions which could safely shut down processes or isolate sections of the water distribution system.
It should not be much of a surprise that the technology for such a system is nothing new. In fact, many are in operation throughout the water industry. You probably have one, as well. It's your SCADA system.
Using a SCADA system to its fullest is the best way for water companies to leverage existing infrastructure and available resources. A major advantage of SCADA systems is that security measures are coordinated with operations.
A SCADA system linked to perimeter monitoring devices can either significantly reduce or eliminate the need for manned patrols. Security systems or equipment, including video cameras, motion detectors, contact switches, keypad entry devices and card readers, can be readily interfaced either directly to the SCADA network or via a nearby RTU.
Security breaches are reported to the operations staff in the same manner as process failures - via the alarm system that is built-in to all SCADA systems. Operators can be alerted by a broad array of visual indications on graphical displays, as well as audible alarms.
Time-stamped alarm records, which are maintained in an audit trail, allow alarms to be correlated with other time-based information, such as video frames. The audit trail is also extremely important to investigations, after-the-fact.
SCADA systems also routinely interface with a wide variety of process analyzers, which could be used to detect the introduction of contaminants to the water supply system. Today's analyzers provide on-line measurements of chlorine, dissolved oxygen, color/turbidity, conductivity, pH, pressure and flow. However, many tests remain offline and much R&D continues. We hope these efforts result in instrumentation, which that would provide live measurements to SCADA systems.
Site Security Measures
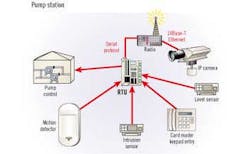
A pump station is an example of a vulnerable area in which an RTU is normally present. Functions of the RTU are generally limited to pump control, using input from flow or level sensors. In some cases, however, some security devices are in place and do interface to the RTU. For example, contact switches (or "intrusion sensors") for a gate, building door and the RTU enclosure door often are wired to discrete inputs and allow the RTU to report an alarm if any is open.
If any contacts open when no water company personnel are known to be in the area, that's cause for alarm. Until recently, this level of security was considered reasonable.
Since wired contacts are easy to defeat, some systems add such measures as a keyless entry device and motion detector. Both devices interface to discrete inputs on the RTU.
Also available are more sophisticated keyless entry devices which that use serial interfaces. They provide additional information, such as the card code or key code. The RTU is not in the loop which enables the door to open. Instead, it records the information in the audit trail and informs operators of the entry can simply record the entry and inform operators or be in the loop, which that controls the door lock. Problematic, however, for many existing RTUs is that they are far less likely to have spare serial ports than discrete inputs.
Video cameras are also an option. While closed circuit television (CCTV) has traditionally not interfaced with SCADA systems, today's digital cameras are compatible with personal computers and can reside on the network.
Internet Protocol (IP) cameras are, by definition, Internet-compatible but are also very easy to drop into SCADA networks which that use Internet Protocol. With some programming effort, digital cameras can also interface with other networks via an RS 232/modem connection. To accommodate bandwidth limitations in the SCADA network, the resolution, compression and frame rate are configurable in the camera.
In some configurations, the IP camera does not even interface with the RTU. It simply shares the wireless Ethernet and transports video images to the SCADA workstations. An operator can view the video image as a window on the same screen as other windows, which show a graphical display of the pump station, an alarm list and other information.
As far as SCADA systems are concerned, IP camera technology is still new. While cameras are not currently used in most systems, they can be readily accommodated if the SCADA system supports FTP (file transfer protocol) server capability.
For many water system installations, use of a camera is debatable. A small, fenced-in area such as an elevated tank or pump station is well served by a combination of intrusion sensors and a motion detector. Cameras are more appropriate for perimeter monitoring and open areas, in which the video can distinguish intruders from animals and other motion that is no cause for alarm. For audits or investigations, video also offers the benefit of an image archive.
SCADA Security
If utilities are going to count on their SCADA systems for security measures, the question is, how secure is the SCADA system itself?
Many practices typical in the SCADA world are, in fact, perfect for security. SCADA systems very commonly employ measures such as back-up power systems, redundancy, distributed workstations, password security and remote paging.
For instance, if equipped with a backup battery, RTUs will continue running if the power fails and immediately report a power failure alarm. If communication to a vulnerable area becomes disabled, a typical SCADA system will quickly detect the fact that it cannot communicate with that particular RTU. This puts the site "in the dark," a cause for immediate attention.
If the network is cut off, controllers and RTUs simply continue monitoring and controlling their processes. Once communication is re-established, many RTUs are able to report alarms, events and historical information over the time that the network was out of service.
Remote sites, such as pump stations, can also use redundant networks. For example, CDPD or dial-up can back up a leased line. Communication networks that use two different technologies can be difficult to defeat. An excellent combination is one that uses both hard-wire and wireless communication. This keeps the site "out of the dark" but you have to decide if it is worth the cost.
In many SCADA systems, the fact that the networks are private provides a great deal of security. Hackers simply cannot access the network from an off-site location. Keeping SCADA computers "disconnected" from the outside world, including the Internet, isolates the system from an awful lot of risks.
However, off-site workstations can be extremely valuable in the event that the control room is disabled. Workstations can be located not only elsewhere in the water system but also at home. Wherever the workstation is located, the user must enter a password. To ensure this is not the weakest link in security, management must establish passwords, other than the defaults, and periodically change them.
It is important that off-site access be limited. Command sets can be proprietary and restricted. If capabilities such as programming and downloading are available, hackers can potentially do a lot of damage.
The only problem today is that there are too many benefits in connecting to the outside world. Numerous information services are available via the Internet. Equipment suppliers can perform maintenance via the Internet. You can make operations information available anywhere in the world. If you want your system "connected," prudent use of firewalls and cyber security measures is mandatory.
Many users feel secure because of the proprietary nature of their systems. "Cryptic" command sets, communication protocols and programming tools can be sufficiently discouraging. But we have seen the results of work by determined terrorists. Anyone willing to invest the time can figure out proprietary systems.
The question is what terrorists could accomplish by accessing the SCADA system. By changing process operations, they can cause major nuisance problems, damage process equipment and cut off service to your customers. However, this activity is more in the realm of hackers and disgruntled employees. The widespread harm sought by terrorists can only be accomplished by introducing outside agents to the water supply. Therefore, securing vulnerable areas is the priority.
Enhanced Use of the Scada System
Since the real risks are not in the SCADA system but in the process, how can you further use the SCADA system to reduce process risk?
In its most simple implementation, a SCADA system can distinguish between normal and abnormal operation. Even basic monitoring functions include discrete, limit and rate alarms. As in the pump station example, control actions can also be verified and alarms set to indicate failures.
Alarm limits can also dynamically follow the process. For example, a ratio alarm could be set if the chlorinator feed rate were inappropriate to the water flow rate, even if it were within fixed high and low limits. If someone tampered with the chlorinator setting, this setup would catch it and report an alarm. Note that a chlorine analyzer further downstream should also back up this system.
Perhaps the most advanced functions are performed when the SCADA system is used in conjunction with a modeling and simulation system. If the SCADA system is networked with the modeling and simulation system, it can provide live process information to build a model of your entire distribution system.
The model can be used to establish feed forward controls and run the process with increased efficiency. It can also provide for back-up alarming. If a process alarm, e.g. for a pump failure, does not work, the inevitable effect elsewhere in the system can still result in an alarm, which reports the pump failure as the likely cause.
Security issues are making simulation significantly more important than in the past. Now emerging are techniques that use the model to simulate addition of contaminants at various points in the system and how they move through it. In an actual event, this information should help verify the point of contamination and determine actions at sites, such as pump stations, to isolate the appropriate section of the distribution system.
About the Author
Kevin Finnan is Director of Marketing at Bristol Babcock in Watertown, CT. He has significant experience in measurement products and SCADA systems. Over 21 years with Bristol Babcock, he has been a systems engineer, instructor, industry manager and product manager.